Audit
Objectivise
Audit aims to provide an independent view on some situation (IT, Security, Finance, ...). Stated otherwise, we provide to the Customer a picture of the situation without shade.
For Cybersecurity, several techniques are at our hand. We often take a few days (3 to 4 days) to have a good estimation of the Cybersecurity posture of the Organization. By means of an external Audit request on some part of the organisation or by some certification like ISO-27001, ISAE-3402, ... (which are in fact external Audits), the Organization proves that it is possible to attest that some processes are always conducted. Those assessments can be executed with different strength : light, table-top, in depth
Light - Theorical / Table top - in depth
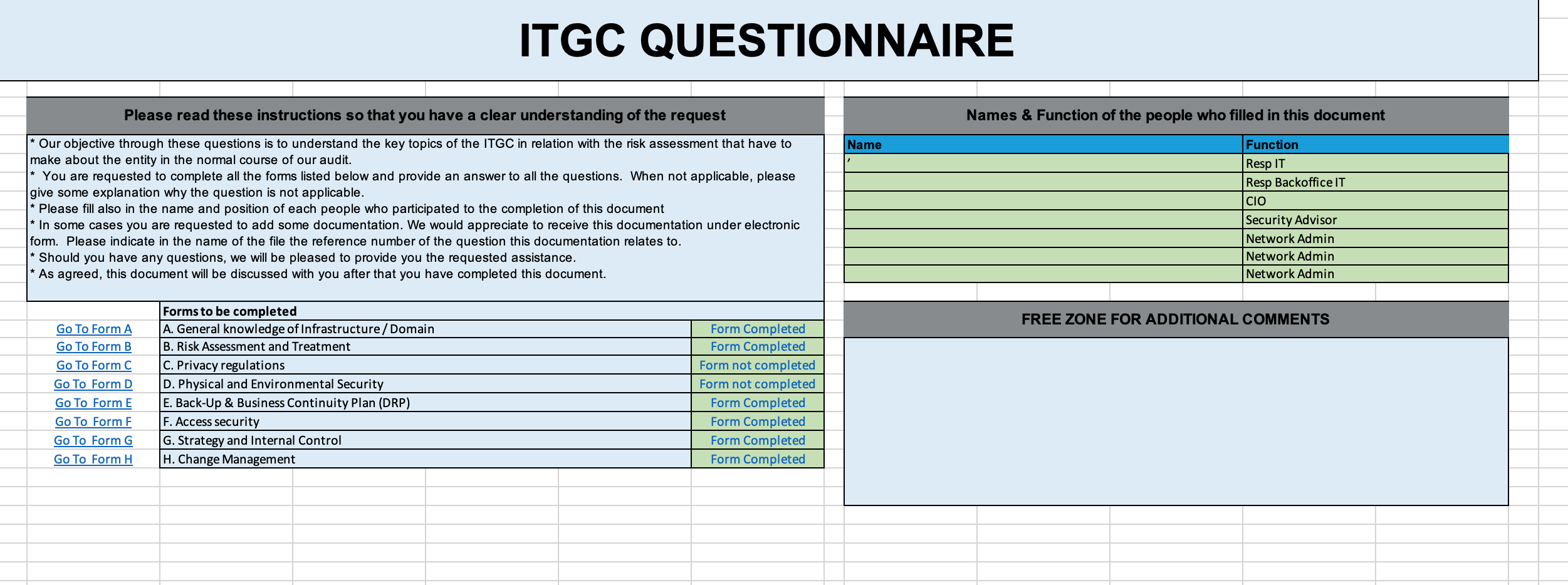
Light evaluations (light assessments) are execute over a couple of hours (for very small enterprises or limited process) à quelques jours (moyennes entreprises). Généralement, l'Audit commence avec une ou plusieurs rencontres avec les donneurs d'ordre : CEO, CIO, CTO, DPO, Assureur, ... afin de leur demander leurs attentes quand à ce qui va sortit de l'Audit et le niveau de maturité attendu.
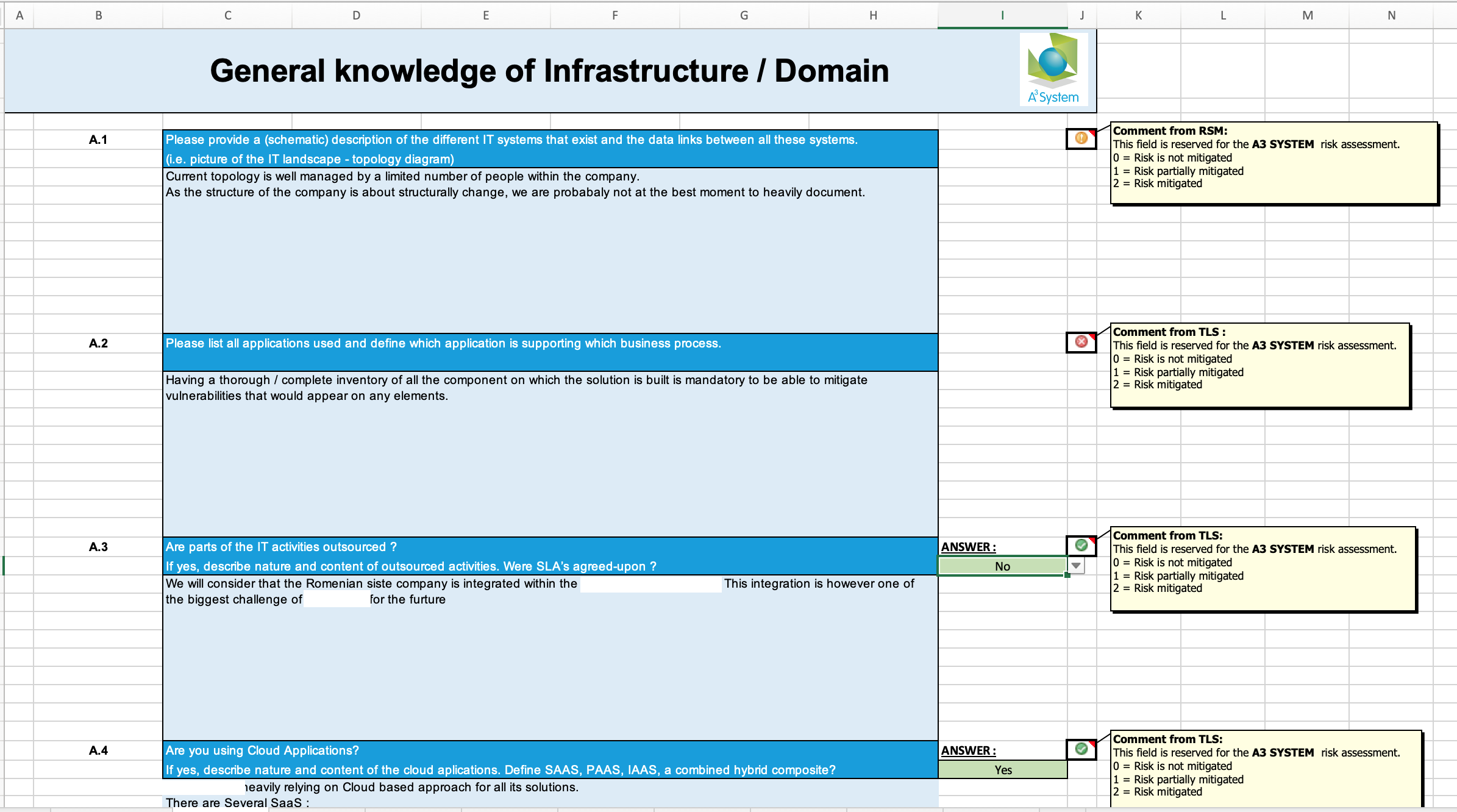
Based on a check-list, control points are reviewed either in self evaluation mode by the Team members or by the Auditor or the auditor investigates based on questions. One should expect answers to be often biaised.
Audit often takes into account the different axes as one can see on the Evaluations sheet :
- Do the team members know their environment ?
- Do they (correctly) evaluate the risks ?
- Is the privacy of the data sufficiently taken into consideration ?
- How is the Physical security taken into account ?
- Are the Key processes identified (this is the Business responsibility) ? Are the necessary IT Harwares & Softwares identified to ensure that the Business Continuity can be guaranteed ?
- Are the Access Secured ?
- Physical access ?
- Logical access ?
- Technical access ?
- ...
- From our technical background, we can usually either provide direct support or execute the audit mission.
- What strategy has been chosen & implemented for the internal access control ?
- How are the changes managed ?
Every single points must be evaluated with a grid with levels of 3, 4, 5, ... levels to evaluate the maturity of the process.
Data privacy issues should be treated separately to ensure the best management. A quick overview might not be sufficient & a deeper review requires qualified person.
From the Audit exercise, we come up with a maturity diagram along the axis of concerns. 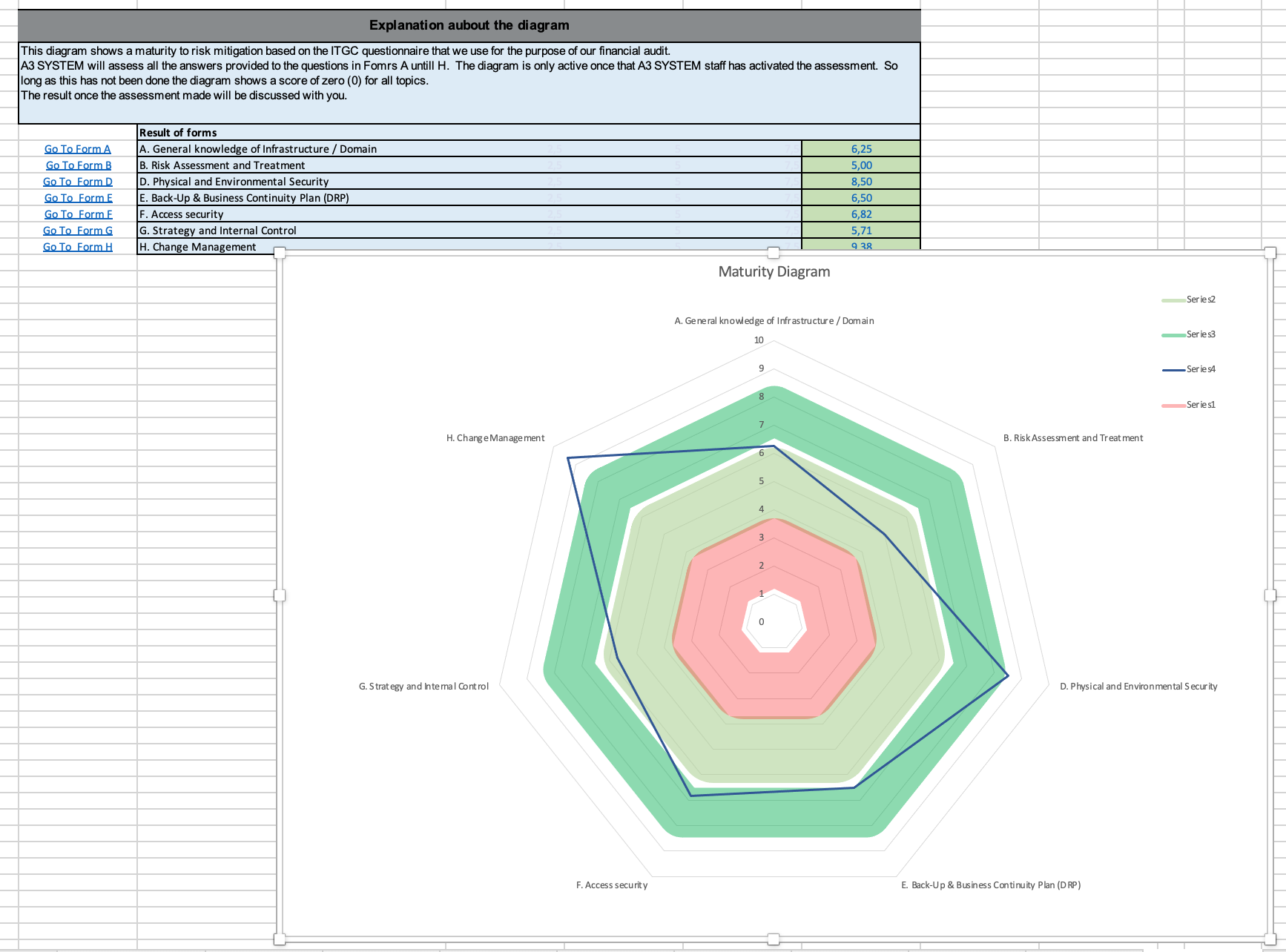
We can propose you to define a matrix of expectations : You do not expect your Cantine supplier to have the same level as the one provide your software to manage key element of you organisation.